Security groups, the absolute basics
This tutorial is part of the Cloud Starter Series.
Back to Cloud StarterCategory: Beginner
Difficulty: 1 out of 5
Duration: 15 minutes
Find a mistake? Let us know the issue here.

Inspect your Security Groups
Access to Nectar Research Cloud resources is organised in projects and there are a few different types of them. If you’re reading this, it is likely that you are using a personal trial (or pt-) project. If this is the case you probably already have some pre-configured security groups.
If you’re in a project with other users, then it is possible that they have already created Security Groups and Rules.
With the steps below you’ll inspect your existing Security Groups and Rules.
- Logon to your Nectar Dashboard at https://dashboard.rc.nectar.org.au
-
Ensure the Project Selector (top left hand side of the page) indicates the project you want to work in:
- Navigate to
Project/Network/Security Groupsin the navigation panel on the left hand side.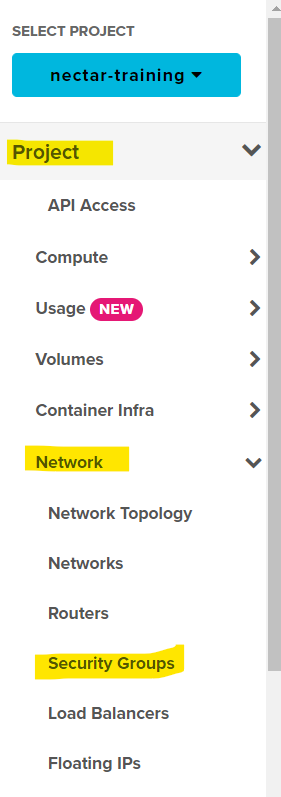
You will now see a list of the Security Groups that are available in your project.
Separate across projects
Your security groups are separate across your Cloud projects. For example, if you created some security groups in your Project Trial, these would not appear in other projects you are a member of.
SSH group By the end of this tutorial you need to have a Security Group that will allow you to connect to an instance using SSH.
If you see a group that is named ssh or similar, then
- Click the
Manage Rulesoption in the Action Menu button beside this group
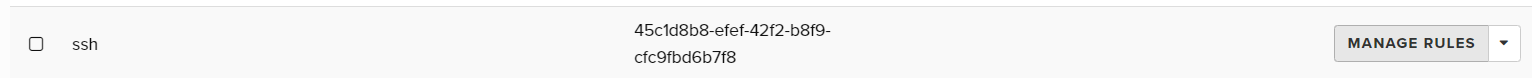
A list of Rules is displayed that are part of this Security Group.
If your Security Group contains this rule, then your project is all set for launching an instance and connecting via SSH. The next two sections are optional for you, but we do recommend you give them a go: there is every chance that at some stage in your Nectar career you’ll use your skills in creating and adjusting security groups and their rules.

If you didn’t find a group named ssh or similar, or didn’t find a group containing the the ssh-ingress rule as above, then you should proceed with the next two sections, where you’ll learn how to Create a Security Group and Create an ssh rule.